A while ago, I created a graphic on Insider Risk Management, one of the solutions in Microsoft Purview. This blog post adds a bit of context to that graphic.
Insider Risk is a concern in the world of corporate espionage, detecting fast and early is key to potentially stopping a malicious or disgruntled insider from stealing company secrets, causing irreversible harm to business.
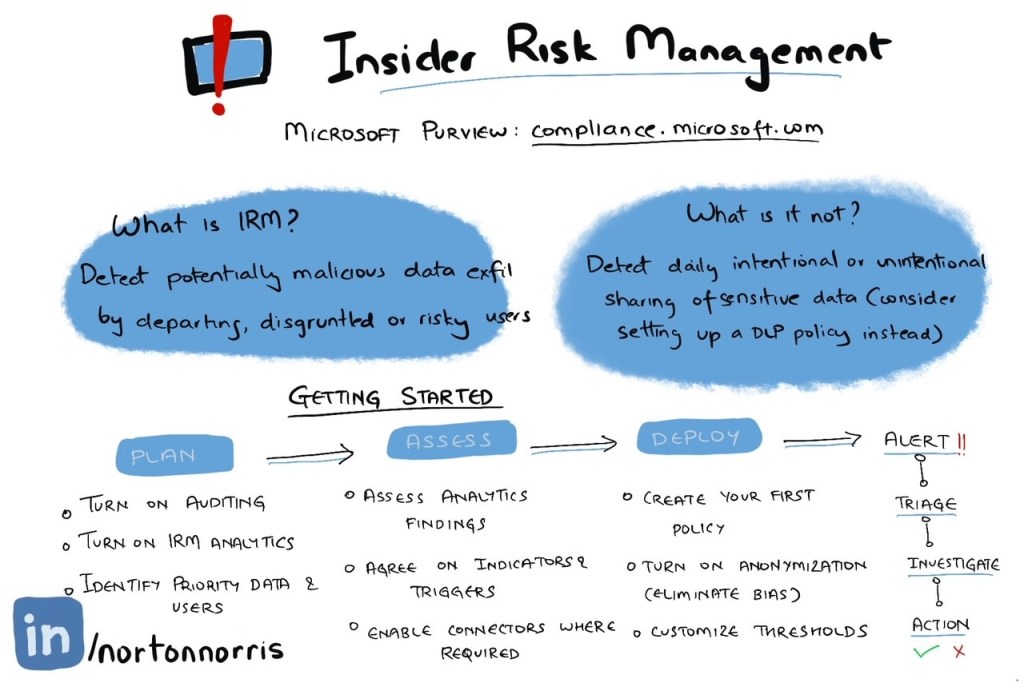
Insider Risk Management (IRM) from Microsoft is one of the solutions available with the E5 or Compliance E5 license. A plus point to this solution is how well it works together with signals from solutions such as DLP and Communications Compliance.
Starting fresh? First up, turn on Analytics. This can be found in the settings menu of Insider Risk Management. This starts analyzing patterns within activity logged in the audit log. Once the initial analytics scan is complete, you will see a list of recommended policies to start.
Start early by identifying priority users to monitor, as well as locations where business secrets are located, update these indicators under the Insider Risk Management settings menu.
If you are starting with a proof of concept (PoC), turn on all available indicators. Note: Device indicators can be enabled if your devices are onboarded to M365 Purview or M365 Defender. Turn off anonymization. This will help you weed out the false positives from your PoC testing efforts.
Looking to connect your HR data to detect events like data theft from departing users, or unusual physical activity using badging data? Look at the available connectors in Microsoft Purview.
We previously turned on Analytics, which provided a list of recommended policies. Start by creating your first policy, target a pilot user group, or all users in your organization. Turn anonymization back on, eliminating bias when investigating potential insider threats.
Are you seeing too many false positives? Adjust the detection thresholds.
Communications Compliance under Microsoft Purview detects activity such as harmful or inappropriate language in the workplace. This feeds risky user signals into Insider Risk Management.